You wear a Fitbit during your jog in the morning, swipe your grocery loyalty card when you checkout in the evening, and share your contacts when you play Candy Crush at night. This “Internet of Things” offers automation, customization, and convenience and, in turn, demands access. The daily choices to allow access or not repeatedly require you to produce the contours of your private life, to open certain spaces and keep others closed. In this collaborative potluck, we asked: how do those contours take shape? (If your first question, is what the heck is a critical potluck? In short, it’s a workshop-like collaborative event; this one was held on September 15 at Bard. Check our handy guide for more details.)
We began with an object of inquiry: Part 4 of the Pew Research Center’s Internet Survey. It was conducted on 461 participants between Jan. 27 and Feb. 16, 2015. The survey offers a snapshot of how people face the ever-growing number of technologies and products that make claims upon various types of private information (from your Google search history to your average driving speed). Pew released the survey data with summary analysis that provides a glimpse of the general sentiments of respondents. (Hover over the pie charts to see the corresponding questions.)
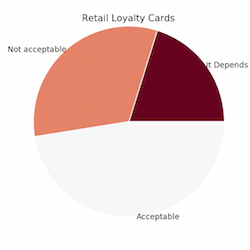
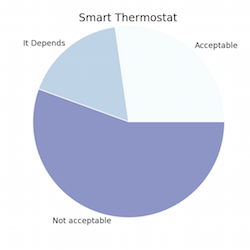
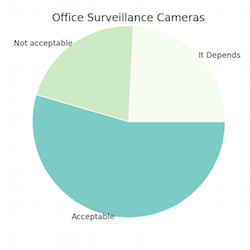
The aggregated responses illustrate that, for instance, most people are more wary of potential encroachments to their homes than their workplaces. The critical potluck, however, was intended to interrogate more subtle patterns that might be observed in how respondents conceived of that fuzzy line between acceptable and creepy. The task was to pose a question to the survey data designed to generate results that reveal points of tension in how survey respondents constitute their private lives. Consider the great number of scholars who have examined the boundary between public and private—Michel Foucault, Jurgen Habermas, Nancy Fraser, Michael Warner, and so on. Many of these writers have discussed the relationship between public and private in terms of sites, spaces, or spheres. In The Human Condition (1958), Hannah Arendt claims, “the four walls of one’s private property offer the only reliable hiding place from the common public world, not only from everything that goes on in it but also from its very publicity, from being seen and being heard.”1 Private spaces are homes, glove boxes, and safe deposit boxes. What happens to the language and concepts of privacy when it is represented in 1s and 0s and distributed across databases and server farms?
The potluck discussion began with this familiar idea of a private space: Is it strange that a smart thermostat is so much more worrisome than workplace cameras that use facial recognition algorithms? But as we worked through more of the responses, participants became more interested in a peculiar incongruence in the charged, aggressive manner that respondents discussed such fuzzy, abstract ideas, like their data, information, and even stuff.
Rather than just look at specific lexical patterns, though, we wanted to track what kinds of words and constructions were used to describe emergent notions of privacy. We ended up turning to Docuscope, a dictionary of over a hundred abstract categories (what the designers call Language Action Types, or LATs) that can classify over 40 million linguistic patterns according to their rhetorical usage. Docuscope was designed by Carnegie Mellon rhetoricians, David Kauffer and Suguru Ishizaki, and they describe it as a tool for, “corpus-based rhetorical analysis.” We uploaded the survey responses to the web-based tool, Ubiqu+Ity, which tags the text according to the Docuscope categories. Here’s how one tagged response looks:
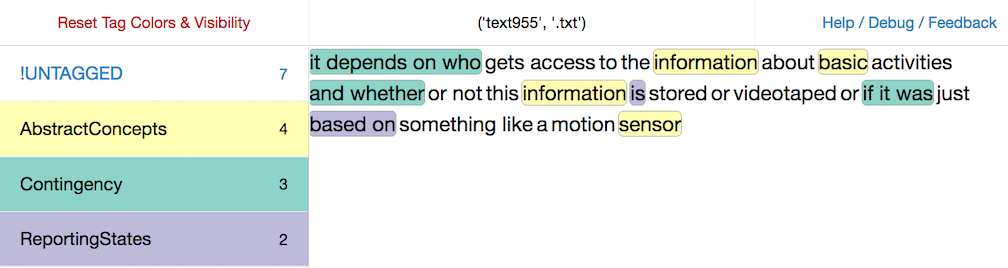
The interface of tagged responses provided more precise vocabulary for describing the relationship between exclamatory adjectives and vague nouns that seemed to recur in the survey answers. Abstract concepts is the most frequent LAT in the data, and Reporting States, Negativity, and Deny and Disclaim are also very prevalent. In this example contingent verb constructions shape how the respondent relates to abstract ideas of “information” and “basic activities.” The respondent considers the different variables at play that would determine whether being monitored via video at work would be acceptable or not.
When the scale of analysis is shifted from individual responses to the LATs in the larger corpus, it appears that the Contingency category best explains the variation among the answers. The graph below is a plot of all 1085 text-box responses to the survey. The points are positioned according the frequencies of every LAT categories in each response. This means that each data point initially has over a hundred dimensions in which it could be plotted, but, of course, there’s no way to present this virtual space and make sense of it. Instead, I’ve reduced the space to two dimensions using the statistical technique of Principal Component Analysis, which produce two new composite axes (made up of a combination of the original 100+ axes) that represent the greatest spread of the data, the most variation in values along one axis and then the axis that is orthogonal to the first axis. These are the principal components.
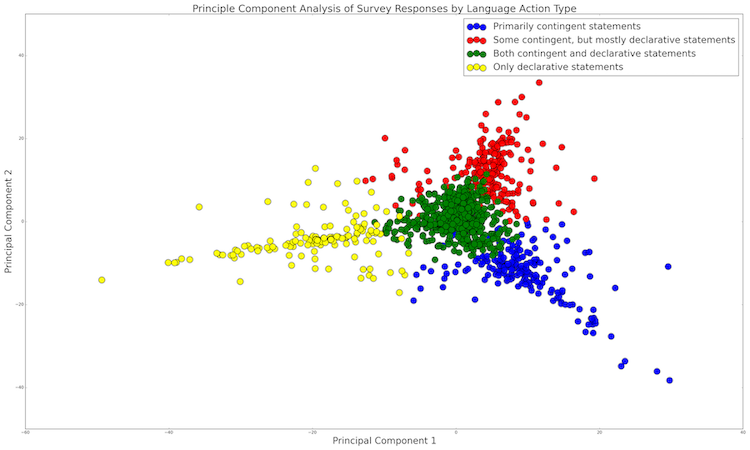
By examining the LAT categories that have the greatest ‘pull’ on the data, we can observe that, along the x-axis, the presence of Contingency language category seems to explain that most difference between responses. Points positioned to the left of the zero on the x-axis refer to answers that have virtually no words or phrases tagged as Contingency, while most of the points to the right, especially in the blue cluster have a relatively high frequency of contingency-tagged terms. Below are representative responses for different areas of the graph, and you can look at the other LAT categories that contribute to the variation between responses here for more details.). For the rest of this brief analysis, though, I want to consider how contingency operates in the survey answers. This result raises a new question: What’s at stake in contingently conceiving the contours of one’s private life? The responses on the right side of the graph indicate participants imaginatively delimiting what ought to be private.
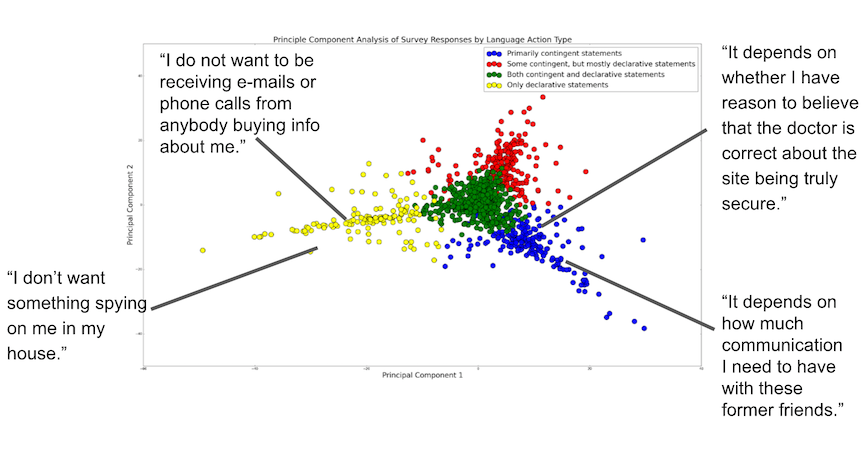
The Contingency tag often refers to responses written in the subjunctive mood, which, as the Oxford English Dictionary reminds us is a grammatical form used to “denote an action or a state as conceived (and not as a fact) and therefore used to express a wish, command, exhortation, or a contingent, hypothetical, or prospective event.” (I like this definition because it acknowledges the use of the subjunctive for both prospective situations and command, which gestures to the angry frustration exhibited in many of these responses.) Psychologist Jerome Bruner observed, “To be in the subjunctive mode is to be trafficking in human possibilities rather than in settled certainties.”3 Contingency in the responses tends to correlate with Abstract Concepts and Reporting Events, creating a profile that is similar to the tagged example included above. Here are other representative answers:
- “I feel like this information would be used against me if I got into an accident. For example, the insurance agency will look at the data and say that I was speeding right before the accident and claim that the accident was my fault. I also feel as though law enforcement would attempt to use this information in the event of a criminal case.”
- “If they just tracked employee attendance and performance for statistical purposes I would be fine with it. But if they used that footage to punish employees that show up late/goof off then I would not be okay with it.”
Part of what is interesting about using the presence of contingent language for separating responses is the fact that taking a suppositional stance turns out not to be very popular perspective, despite the fact that almost all of the questions are phrased in the subjunctive mood. Sixty-eight percent of the respondents did not use any contingent language according to the Docuscope tagger. In the survey, the more common stance is a flat out denial of any demands upon one’s privacy (though this seems unlikely to be as common in real-world decisions). Contingent answers, by contrast, exhibit a willingness to play along. The Pew Research Center administered this survey digitally, with participants recording their answers at computer terminals. Indeed, responses even begin to suspect the survey itself as a privacy violation at times.
“I do not want to give any answer to this.”
This arrangement is fitting since the method of the survey conveniently echoes the typical media interface in which commercial demands are made upon privacy – the screen. Media historian Lisa Gitelman links the plane of the screen to what Walter Benjamin calls the ‘dictatorial perpendicular’ of modern reading.2 Locating the screen in its natural post-capitalist habitat, Gitelman explains that “the office walls contain cubicles, the cubicles contain screens, the screens contain windows, and the windows contain page images. These vertical surfaces nest within each other, interfacing like a sequence of Russian dolls, waiting to funnel attention toward documents as if their very perpendicular sequence could ward off distraction” (130).
Even outside of the workplace, screens prescribe conditions of attention and use that proliferate the number and kinds of spaces in which private content might reside. Contingent responses to the Pew Survey index users grappling with the circumstances of new and vulnerable private spaces.
One response to a question regarding access to one’s phone camera and location:
Because it is not a good idea. By giving anyone access to our camera and your location would mean they could activate your camera anytime without your permission. This means they could spy on you any time they wanted to without your knowledge. To me, this would be a huge invasion of privacy.
In the emergent environment of digital media, privacy cannot properly be delimited to a physical space (although the vehement rejections of any type of home monitoring in the survey responses indicate that this circumstance has not been accepted calmly). Being connected creates a paradoxical condition for privacy. As media theorist Wendy Chun suggests, “Internet users are curiously inside out — they are framed as private subjects exposed in public.”4 Digital media is governed by a “logic of containment, which is always imagined as already transgressed” (13). The word imagined is key here. Private material, data, information is distributed, networked, and re-sold to the point that we can really only imagine the borders of our private lives. The concept of privacy might then be more accurately located in the context of performance, play, heuristic, or supposition, rather than in Arendt’s four walls. It is fluid and demands to be continually re-defined, re-constituted, and re-imagined.
With significant planning assistance from Gretta Tritch Roman and potluck contributions from Maria Cecire, Adhaar Desai, Miriam Felton-Dansky, and Natalie Desrosiers.
References
1. Hannah Arendt, The Human Condition, 2nd ed. (Chicago: University of Chicago, 1958), 71.
2. Lisa Gitelman, Paper Knowledge: Toward a Media History of Documents, (Durham, NC: Duke University Press, 2014), 129.
3. Jeremy Bruner, Actual Minds, Possible Worlds, (Cambridge: Harvard University Press, 1987), 26.
4. Wendy Hui Kyong Chun, Updating to Remain the Same: Habitual New Media, (Cambridge, MA: MIT Press, 2016), 12.